For 2024, Google and Yahoo are rolling out updated guidelines for bulk email senders, aimed at boosting deliverability and fighting the good fight against spam. This is good news: not only will it positively impact your deliverability, it’s easy to implement.
Why the update?
It’s simple: to create a cleaner, more secure environment for both senders and recipients. The new requirements fall into three key categories:
-
Authentication: Email authentication verifies you’re a legitimate sender, not a spammer. If you’re sending emails already, you’ve probably already taken the first step by setting up SPF (sender policy framework) and DKIM (domainkeys identified mail) records, even if you weren’t sure what they did. Now, the next crucial step is publishing a DMARC policy.
-
Simple unsubscribes: No more requiring users to authenticate or navigate labyrinthine unsubscribe processes. One-click unsubscribe provides a better user experience. Luckily, if you’ve already been offering this option, you’re already ahead of the curve!
-
Spam complaints: If you’re diligently collecting opt-ins with proper consent, spam complaints likely won’t be a concern. But it’s always good practice to maintain a healthy email list and engage your audience thoughtfully.
So what is DMARC?
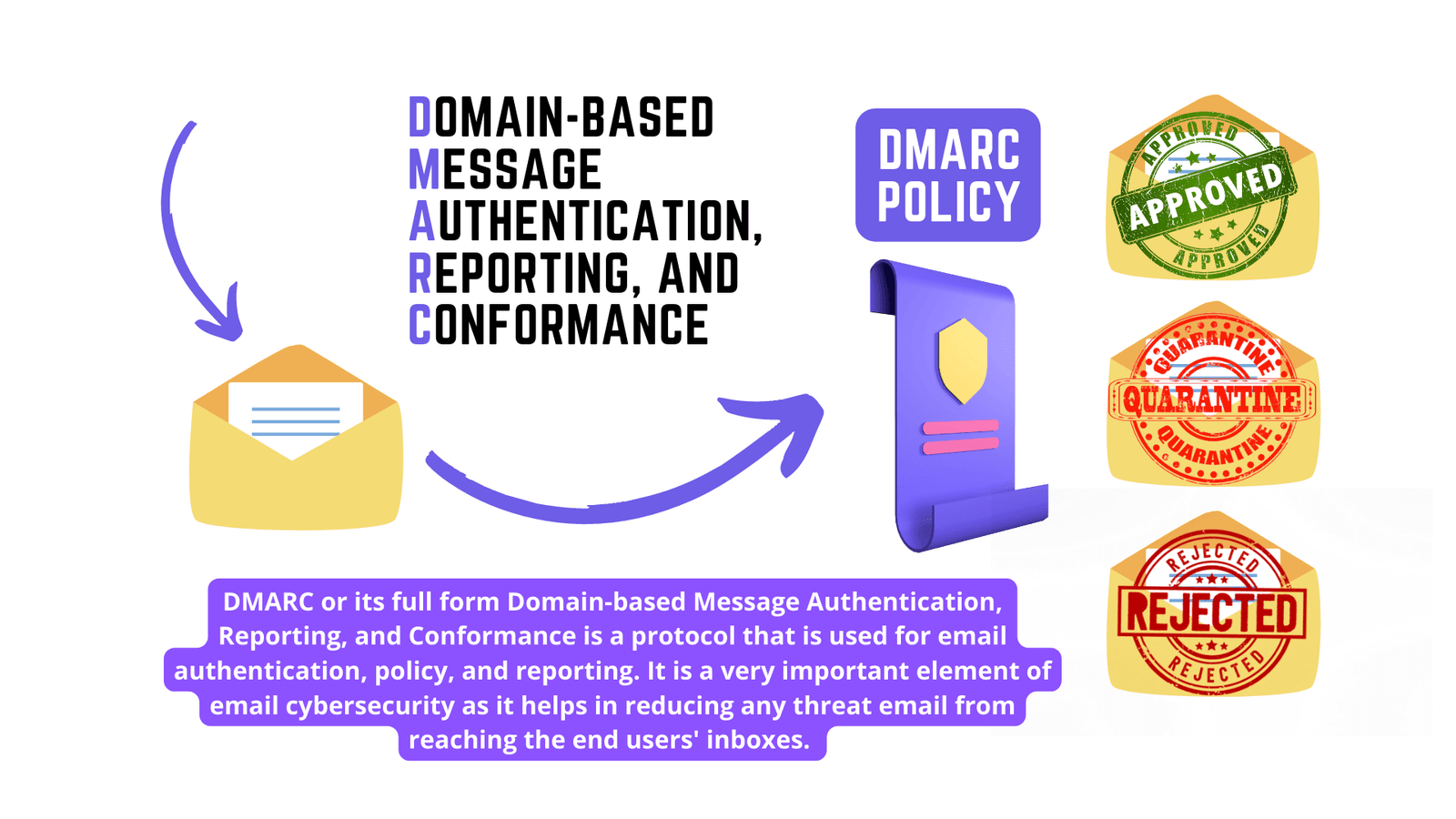
- The DMARC policy (Domain-based Message Authentication, Reporting & Conformance) acts as your email’s official security document, telling the world how to handle messages claiming to be from your domain.
- Setting it up properly is essential today because many Email List Providers (such as small businesses) are already being surprised that their E-Mail Success % Rates Are Decreasing Just This Week (Google and Yahoo Domain Emails Began Enforcement On February 2nd, 2024).By February 1, 2024, publish your DMARC policy with your domain provider. Ensure this TXT record is added to your DNS settings with “yourdomain.com” replaced with your actual company domain:
Hostname: _dmarc.yourdomain.com Value: v=DMARC1; p=none;
It is actually straight-forward for most technical savvy folks whether you manage DNS yourself or need to put in a ticket so that your IT team can handle the DNS settings. (You can learn even more about DMARC records, including other options like adding a “rua” value to designate an email address that will receive DMARC reports, in Google’s documentation here.
These new email requirements might seem like extra hurdles, but they’re ultimately a positive step towards a more reliable and enjoyable email experience for everyone. By taking the small steps outlined above, you can ensure your business thrives under the new rules, reaching your target audience effectively and building lasting relationships.
TECHNICAL DETAILS ABOUT DMARC IF YOU WANT TO DIVE DEEPER:
-
Domain-Based Message Authentication, Reporting and Conformance (DMARC) is an email authentication policy that protects against bad actors using fake email addresses disguised to look like legitimate emails from trusted sources.
-
DMARC makes it easier for email senders and receivers to determine whether or not an email legitimately originated from the identified sender. Further, DMARC provides the user with instructions for handling the email if it is fraudulent.
-
WHY SHOULD ORGANIZATIONS LIKE YOURS BE INTERESTED IN DMARC? Phishing and Spearphishing are among the top attack vectors for any organization dealing with PII (Personal Identifying Information), which can lead to identity impact, financial fraud, or even protected health information (PHI) breaches and Health Insurance Portability and Accountability Act (HIPAA) fines --> why? Because many individuals in the "black market" underground will access, buy, and sell that PII for non-Citizens/those who do not have health insurance-->they will be using it for their own "services" with fake ID presented as the same name and person that your company revealed their PII. Summary: Your/Your Company liability can be far more reaching than you could ever imagine. It happens every day in the United States where "Joe" walks up to the urgent care or hospital needing emergency care with someone else's ID/SSN/healthcare insurance information all for the right price!
-
Fraudulent emails are easy to design and cheap to send, which gives threat actors incentive to use repeated email attacks. DMARC provides an automated approach to reducing fraudulent email, before it ever reaches an employee’s inbox. In addition, DMARC helps prevent adversaries sending email to your organization or others purportedly from your staff.
-
HOW DOES DMARC WORK? DMARC removes guesswork from the receiver’s handling of emails from non-authoritative email servers, reducing the user’s exposure to potentially fraudulent and harmful messages. A DMARC policy allows a sender to indicate that their emails are protected by Sender Policy Framework (SPF) and/or Domain Keys Identified Message (DKIM), both of which are industry-recognized email authentication techniques. DMARC also provides instructions on how the receiver should handle emails that fail to pass SPF or DKIM authentication. Options include sending the email to quarantine or rejecting it entirely.
-
DMARC provides the receiver with an email address to provide feedback to the sender. Potential feedback can include that the sender’s email was rejected/quarantined by the receiver or that a threat actor is attempting to imitate the sender’s domain.
-
HOW CAN I ADOPT DMARC ON MY DOMAIN? Savvy organizations that adopt DMARC do so in strategic stages, with feedback loops between IT departments and their staff (depending on the size of the organization of course!). Because DMARC can block third parties delivering mail on the purported sender’s behalf, some intended messages may be flagged as illegitimate in some cases - which is a very small price to pay (risk vs. reward) in cybersecurity honestly.
Below Are A Few Steps Organizations Can Take To Ease Into DMARC Over Time: 1. Deploy DKIM & SPF in reporting-only mode first, listing known authorized email servers (such as vendors and trusted internal/external Partners). 2. Collect and review reports to identify unknown email servers. 3. Work with business units and IT staff to identify servers and determine their legitimacy. 4. Update DMARC policy flags to “quarantine” then to “reject” as confidence increases that most or all legitimate servers have been accounted for.