My name is Sky and I wanted to thank you for taking the time to visit Sky The Tech Guy, LLC for your Technology needs. For over 20+ years, we have been consistently been focused on our reputation of Guaranteed Quality Technology Services At Affordable Prices and look forward to helping you right now. Please contact us: +1 (678) 671-6378 | FB: Sky TheTechGuy | Help@SkyTheTechGuy.com | Direct Message via SkyTheTechGuy.com
Welcome to our Technology Blog!
Incoming Great Recession For 2025: Are You Diversified?
According to a stunning new survey that was just released, an annual income of at least $186,000 a year is required in order to feel financially secure in the United States today.
Unfortunately, only 6 percent of U.S. adults make that kind of money. So we have a major problem on our hands. The cost of living has become extremely painful, and are stressed out of their minds because their finances are such a mess. Since 2015, we have witnessed an economic shift of epic proportions. The ultra-wealthy have gotten a lot wealthier, the ranks of the poor have exploded, and the middle class has been absolutely eviscerated.
In this current economic environment, only a very small segment of the population is living comfortably. The following comes from CBS News…
Americans have a specific annual income in mind for what it would take to feel financially secure, according to a new survey from Bankrate. The magic number? $186,000 per year.
Currently, only 6% of U.S. adults make that amount or more, Bankrate said. The median family income falls between $51,500 and $86,000, according to the latest federal data. Achieving financial security means being able to pay your bills while having enough left over to make some discretionary purchases and put money away for the future, the personal finance site said.
When I was growing up, I thought that anyone that earned more than $100,000 a year was wealthy.
But now it takes an income about five times that size in order to be considered “wealthy”…
Americans have an even higher yardstick for feeling rich. The survey found they believe they would need to earn $520,000 a year to qualify as wealthy (July, 2024) — up from their $483,000 response during the same survey just a year ago in June, 2023.
Much of the population is trying as hard as they can, but they will never make the kind of money that they would like to make.
Meanwhile, the cost of living just keeps going higher and higher and higher.
As a result, the percentage of Americans that admit that they are experiencing financial stress just continues to go up…
Many inflation-weary consumers continue to experience financial stress, with a new Federal Reserve Bank of Philadelphia survey finding that 35% of Americans are worried about making ends meet, up from 29% a year earlier.
That gap between what the typical American earns and what they aspire to earn means “Americans have their eyes set on this high income, and they think they need to make more money even if they know it’s unrealistic they’ll never make that amount,” Sarah Foster, an analyst at Bankrate, told CBS MoneyWatch.
At this point, even many that are considered to be in “upper-income groups” feel forced to take on extra jobs just to make ends meet…
Americans in upper-income groups are concerned about their ability to pay bills, with more than 15 percent of this demographic taking up additional jobs over the past year, according to a survey by the Federal Reserve Bank of Philadelphia.
As of July 2024, 32.5 percent of respondents earning over $150,000 annually were worried about making ends meet over the next six months, up from 21.7 percent in April of last year, the July survey by the Federal Reserve survey showed.
This percentage is higher than for those in the income groups of $100,000 to $149,999, $70,000 to $99,999, and $40,000 to $69,999. Only individuals who earned less than $40,000, the lowest income group, were more worried than the $150,000-plus group.
I have never seen numbers like this before.
People are feeling so much anxiety about their finances, and that helps to explain why economic issues are playing such a prominent role in this election cycle.
Some Americans are trying to make ends meet by cutting back anywhere that they can.
For example, the following comes from an NPR article about how Americans are cutting back on charitable giving…
Robert Lang, a longtime cabinetmaker in Cincinnati, used to feel good about giving money to less-fortunate people. These days, however, he’s being forced to be less generous.
“I’m no great humanitarian,” says Lang. “But I feel really good if I can give a homeless guy 20 bucks. And we can’t do that anymore.”
The reason? Rising prices, which have forced Lang to dial back his giving as the 69-year-old tries to make ends meet with Social Security benefits and a part-time job with a furniture-making journal.
When times get tough, people become less generous.
I wish that wasn’t true, but that is just the way that it is.
So what will happen when economic conditions become extremely harsh?
BCA Research chief global strategist Peter Berezin is warning that another recession is coming and that stock prices could soon fall by 30 percent…
There may be trouble looming on the horizon for the U.S. stock market, according to BCA Research.
In a note to clients last week (July 18, 2024), BCA Research chief global strategist Peter Berezin warned that, contrary to popular belief, the economy will fall into a recession either during the Election (November, 2024) in early 2025.
Should that happen, the S&P 500 could tumble to 3,750, which marks a 30% drop from current levels.
Will he be proven correct?
I don’t know.
But I do know that it feels like a recession has already arrived to many Americans.
Every day, we get even more bad economic news. For instance, Fox Business just published an article about how major drug store chains are in the process of closing down locations from coast to coast…
Just this week, Walgreens announced that it would close a “significant” number of under performing stores across the U.S. due to ongoing challenges with profitability and declining margins.
Earlier this month, Rite Aid announced that 27 locations in Michigan and Ohio have been added to the growing number of stores it plans to close while it restructures under Chapter 11 bankruptcy.
In large cities all over the nation, thousands upon thousands of commercial properties are now sitting empty.
Of course this is just the start.
As the globe is rocked by one chaotic crisis after another, things will get a whole lot worse.
A “perfect storm” is now upon us, and most people have absolutely no idea how harsh conditions around us will soon become…
Banking On Blockchain: Metallicus Is Bridging Fiat Money & Digital
BRIDGING FIAT CURRENCY WITH LARGE BANKS EMBRACING ISO20022 FINANCE!
The rise of tokenization by large banks
A narrative in the banking industry that has been building momentum for some time now, faster payments, may unlock the key to this merge of centralized and decentralized future for payments. Cryptocurrency, with over $3 trillion dollars in market capitalization and over $153 billion of that being stablecoins, the trend is clear. The tokenization of fiat currencies and real world assets (RWA) is inevitable.

Recently we have seen the rise of tokenization by large banks and funds, most notably the Blackrock Bitcoin ETF and BUIDL fund which essentially tokenizes the US Dollar and pays interest on-chain in USD, invests in cash, U.S. Treasury Bills and repurchase agreements. This is the first large institutional stablecoin offering on-chain, and it goes hand in hand with the securitized version of Bitcoin that trades today as the Blackrock Bitcoin ETF IBIT. This movement by traditional finance into the decentralized world is only the beginning of the marriage between CeFi and DeFi. One can only imagine, over the next decade, we will witness trillions of dollars of asset tokenization, from fiat currencies, to securities, to precious metals and everything in between.
Enter Marshall Hayner, the man with the vision of melding traditional finance and cryptocurrency, who has been hard at work on this problem for over a decade. Hailing from Upstate NY, and attending college at Northeastern University in Boston, Marshall was always fascinated with technology and the internet, particularly decentralized networks and encryption. In 2011 Marshall moved from Boston Massachusetts to San Francisco California and shortly thereafter began working in blockchain. Having been a spectator and hobbyist from the early day of Bitcoin (2009 and on) Marshall envisioned a time in which cryptocurrency would reach mass adoption, and that the early ethos of Bitcoin overtaking banks was incorrect, he believed that banks and consumers would ultimately embrace this technology.
Cryptocurrency, as Hayner saw it, would transform the world of payments through transparency, speed, efficiency and programmability. Marshall launched his first cryptocurrency startup QuickCoin in 2013, a simple, easy-to-use Bitcoin wallet that could be created and managed through your Facebook account. Shortly thereafter he would leave QuickCoin to join Stellar Development Foundation, get obsessed with Dogecoin and eventually go on to create his vision for the future of blockchain, Metallicus.
Fundamental major hurdles to crypto adoption
At Metallicus, Marshall worked with his co-founder, Glenn Marien (who coincidentally built the first Dogecoin wallet Dogechain.info, where they met) and team to begin building this vision for merging traditional banking and blockchain with the launch of Metal Pay in 2018. Metal Pay allowed consumers the first opportunity to have a regulated bank account paired with crypto trading and payments in the US.
With the launch of the Metal Pay app, the Metal DAO, a decentralized autonomous organization, based around the Metal ecosystem began. From the Metal DAO a cohesive ecosystem for banking and payments emerged. A fast and relatively free payments network was needed without gas-fees, that could easily support decentralized identity, and XPR Network was born.
Traditionally, the crypto space had not embraced compliance and regtech (regulation technology), rather it initially favored a more anarchist state. This culture ultimately led to multiple boom and bust cycles in which, eventually the mainstream and the industry itself began to realize: compliance and identity on-chain could actually unlock the keys to massive growth. The blueprint to building the bridge from the world of blockchain to traditional banking was formed.
From this vision Hayner immediately began working with his team at Metallicus to build Metal Dollar (a stablecoin index basket), Metal Identity (a decentralized identity protocol for multiple chains), Metal X (an open source decentralized trading engine), WebAuth Wallet (a non custodial crypto wallet focused on Web Authentication) and Metal Blockchain (a layer zero blockchain that could host public and private ledgers for institutions).
Positioning banks to have their own private ledgers
With the rise of L1s, it became clear, banks would not be launching on existing blockchains, rather their interest remained in having their own private ledgers that could eventually some day interact with public ledgers like Bitcoin and Ethereum. The concept of L0, albeit a relatively new one, is to position the banks to have their own private ledgers which increase efficiency and accountability, while allowing them to settle assets between each other relatively instantly.
Additionally, a notion of decentralized identity for consumer, business and government is critical for maintaining BSA (Bank Secrecy Act) compliance on-chain. The message instantly resonated and Metallicus began to welcome banks and Credit Unions into its ecosystem with the Metal blockchain Banking Innovation program launched earlier this year.
Since then, Hayner and Metallicus have focused on using the framework created by XPR Network (fast instant payments, low resource costs, scalable, decentralized identity) as a template for other banks to launch their own ledgers, while having their own stablecoins and DeFi ecosystems and beyond. XPR Network, ultimately, would evolve to become a subnet of Metal blockchain, forming one cohesive chain.
Metal DAO would go on to pass a governance proposal to form Metal L2, building a bridge between the bulk of DeFi activity on Ethereum and the Optimism Superchain, directly into Metal blockchain. Imagine the day that you could fluidly move a dollar from your checking account to the blockchain, and directly from the chain into your savings account, instantly. That day is coming soon if Hayner has anything to say about it. According to Hayner: he envisions “A day in which we stop working for money, and money begins working for us”.
Google Cloud Accidentally Deletes $125 Billion Pension Fund’s Online Account
Google Cloud Accidentally Deletes $125 Billion Pension Fund’s Online Account
A major mistake in setup caused Google Cloud and UniSuper to delete the financial service provider’s private cloud account.
This event has caused many to worry about the security and dependability of cloud services, especially for big financial companies.
The outage started in the blue, and UniSuper’s 620,000 members had no idea what was happening with their retirement funds.
Services didn’t start again until Thursday, and the fund promised its members that investment account amounts would be updated as soon as possible, even though they were still showing numbers from the previous week.
Joint Statement and Apology
According to the Guardian reports, the CEOs of UniSuper and Google Cloud, Peter Chun and Thomas Kurian, apologized for the failure together in a statement, which is not often done.
“This incident is an exceptional and singular occurrence that has not happened with any client of Google Cloud on a global scale before.” This ought not to have occurred. Google Cloud has implemented preventative measures in response to the identified events that precipitated this disruption.
They said that the event was “extremely frustrating and disappointing” for members and caused by a “one-of-a-kind occurrence” in which UniSuper’s Private Cloud services were set up incorrectly, causing the fund’s cloud subscription to be deleted.
“UniSuper’s Private Cloud subscription was ultimately terminated due to an unexpected sequence of events that began with an inadvertent misconfiguration during provisioning,” the two sources stated. “Google Cloud CEO Thomas Kurian has confirmed that the disruption was caused by an unprecedented sequence of events.”
Best Places To Create AI Art For Free
Generate AI Art For Free: Best Places
Freedom of expression should be free!
Everyone loves to generate AI art, but no one likes to pay for it. GeeksByTheHour.com and Dr. Sky also believe that “Freedom of Expression”, especially through art, should be free! Not just low levels of quality expression, but also high quality art should not cost anyone an arm and a leg to express themselves, their culture, or even showing how they are feeling today.
Here are five places you can go right now to make some pretty pictures that are free to create, but don’t necessarily “look” free!
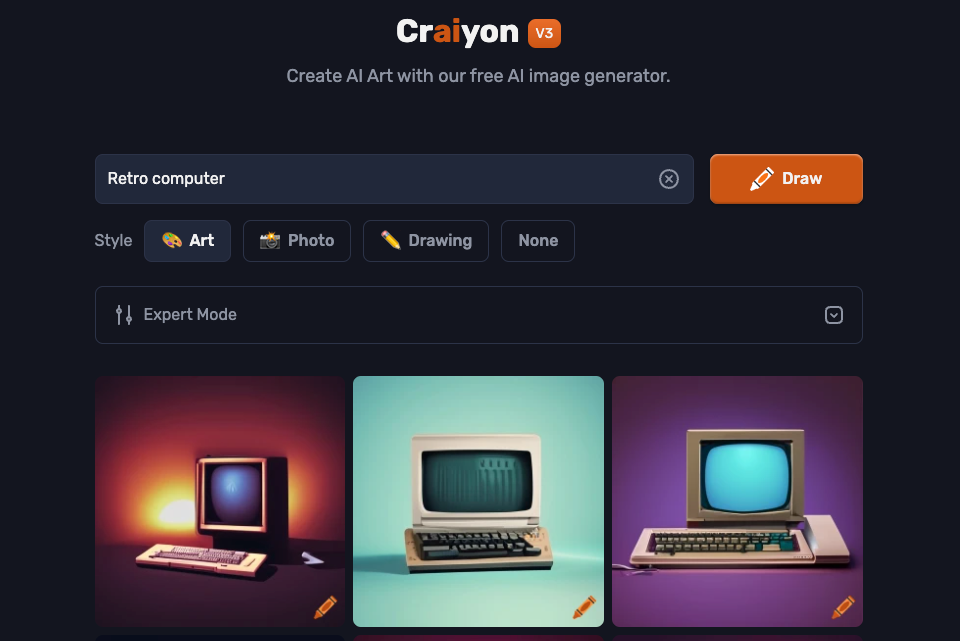
1 Craiyon
This tool used to be known as “DALL-E Mini”, but had to change to Craiyon since the company isn’t affiliated with OpenAI or its DALL-E image generator.
Transparency here at GeeksByTheHour.com is a key value, so we want to be clear – Craiyon does not produce very good results compared to most paid or free AI image generators, but it is the only free option that still has that unique “shaky-ness” that early AI images had. While everyone is approaching perfection with their models, Craiyon has retained that quirky charm, and so deserves some love in my opinion.
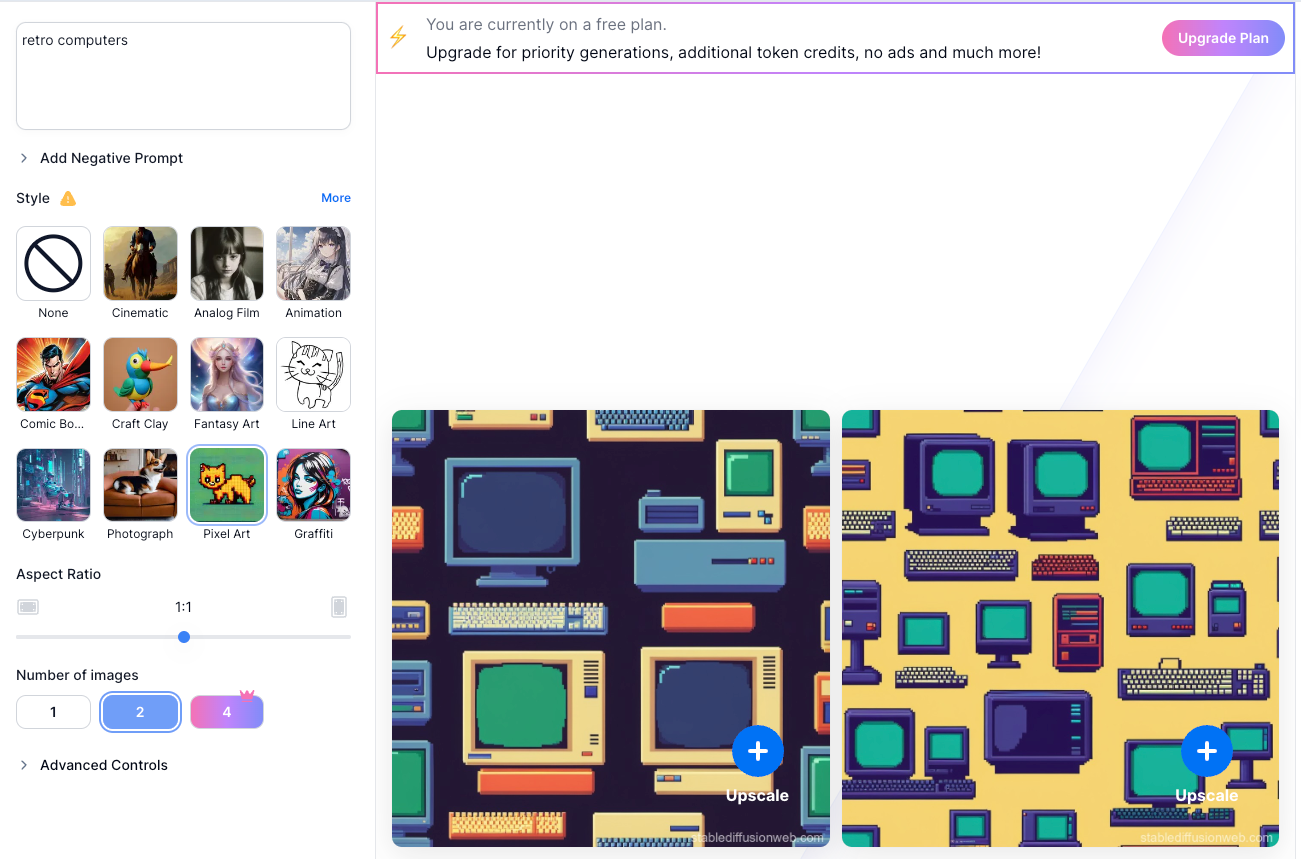
2 Stable Diffusion Online
If you have a GPU with enough memory and performance, you can run Stable Diffusion locally on your computer. If not, or you don’t want the hassle, then you can use this high-end image generation model via Stable Diffusion Online. You can sign up and generate images for free, although you only get a limited number of credits to play with.
Also, on the free plan images have a watermark, but you can always crop that out if you’re smart with the aspect ratio selection. Overall, the quality of the images generated here is great and comparable to paid services like MidJourney or DALL-E.
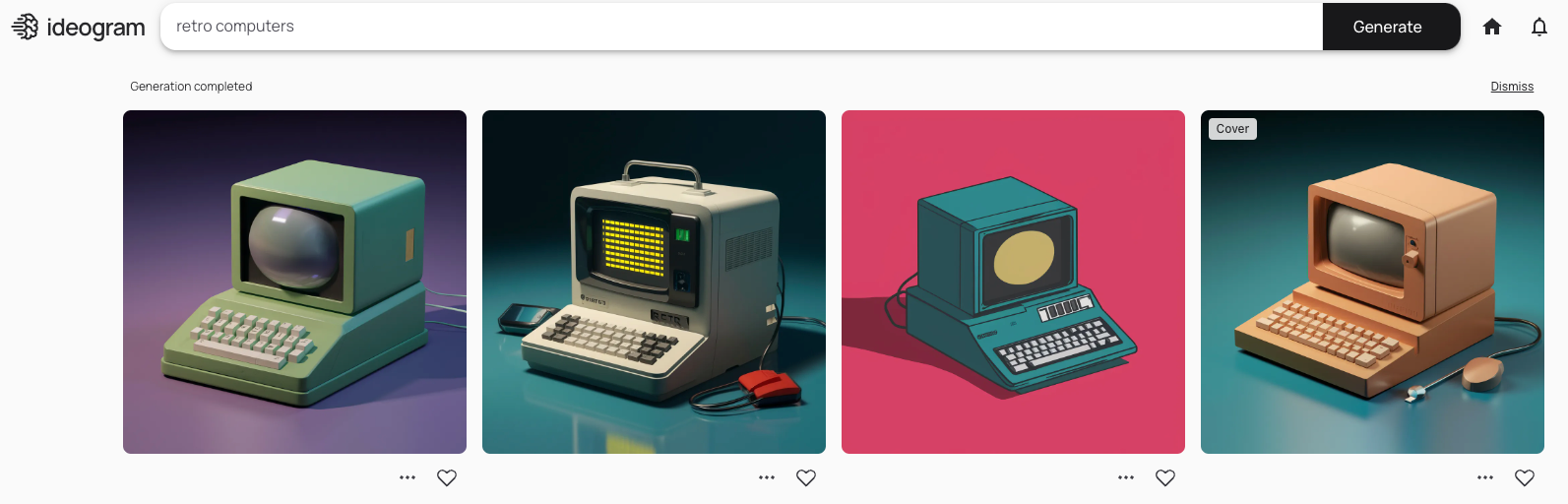
3 Ideogram
Ideogram is a hot new competitor to MidJourney which I found to be quite promising in terms of features, but not quite there when it comes to the final quality of the results or consistency. However, one big advantage Ideogram has over MidJourney is its free tier. MidJourney used to offer a free tier, but has since ended it. So if you want something quite similar, but don’t want to pay for it, give Ideogram a shot. It’s definitely one of the best AI image generators on the market right now.
4 Artbreeder
Artbreeder offers a set of different tools that let you do all sorts of creative things with images. This includes “Prompter” which is the core tool to create images from text prompts. However, there’s some interesting stuff that lets you mix images, create a character with a certain pose from source images, and much more. The output is quite decent, but it works best when you provide your own source images in addition to your text prompt.
The free tier comes with 10 credits per month, but you can get more by earning achievements.
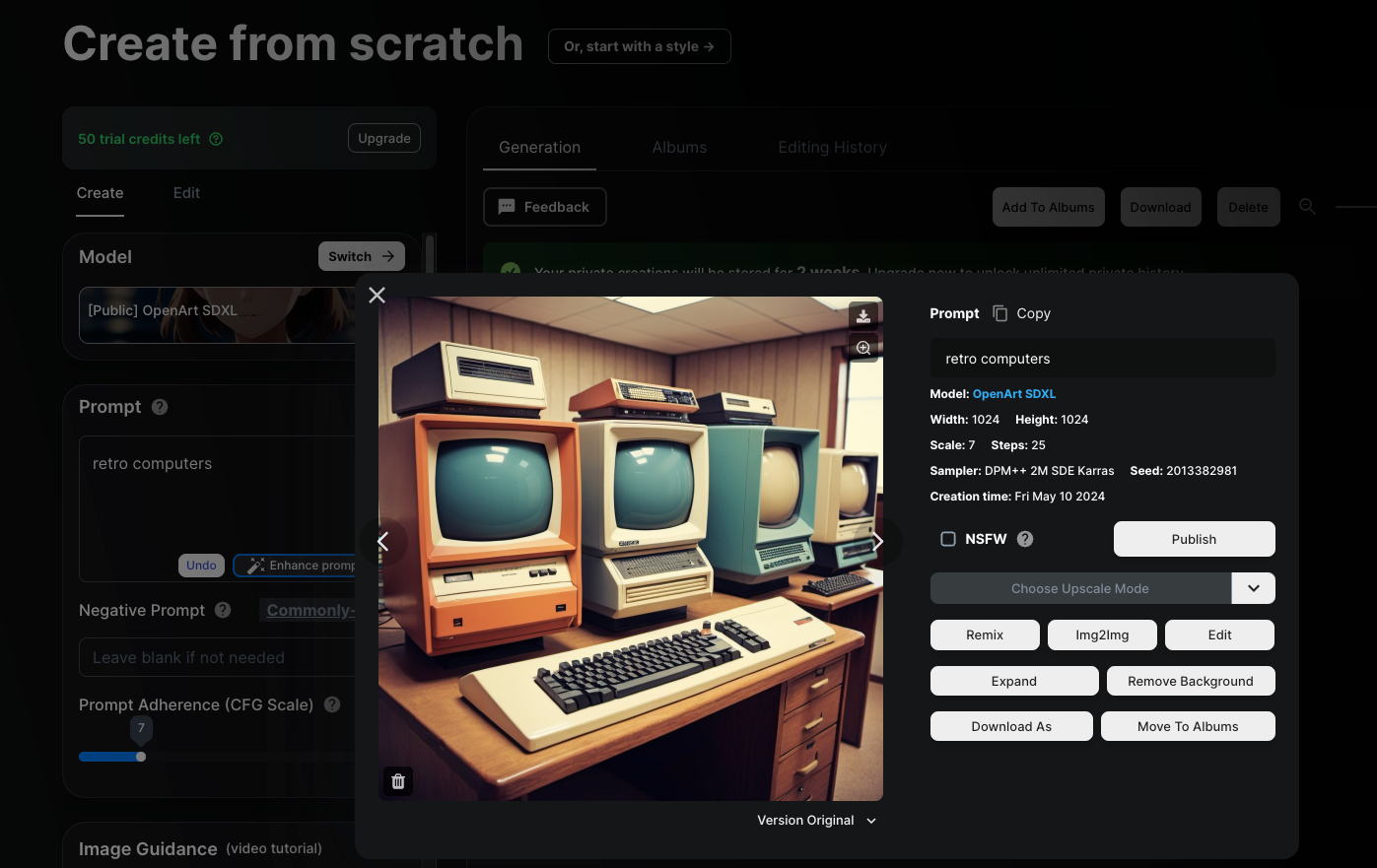
5 OpenArt
OpenArt comes with a 50-credit trial, and if you join the OpenArt Discord server, you’ll get another one-time allocation of 100 credits. These credits let you use all the premium features of the service.
Once you have used up those credits and fall back to the free tier, you will be limited to 50 generations using one of only four models per day. You are also limited in terms of image size.
One major bonus of the free tier for OpenArt is that even images generated on the free tier are private, which is not true for the competition who usually require a paid subscription (and quite an expensive one) to generate images privately.
While you are enjoying those free trial credits, you’ll have access to a mind-boggling number of specialized image generation models, so make the most of it!
While it’s definitely worth paying for a premium art generation service like MidJourney, if you just want to make some AI images for a once-off project, or you want to learn the ins and outs of this fascinating new technology without spending any money, these free services offer more than most people will ever need.
Alert: Dell’s 49 Million Records Breached For Sale (May, 2024)

Dell notifies customers about data breach
Dell is warning its customers about a data breach after an alleged shadowy cyber criminal offered a 49 million-record database of information about Dell customers on a cybercrime forum.
An alleged cyber criminal called Menelik posted the following message on the “Breach Forums” site:
“The data includes 49 million customer and other information of systems purchased from Dell between 2017-2024.
It is up to date information registered at Dell servers.
Feel free to contact me to discuss use cases and opportunities.
I am the only person who has the data.”

- The full name of the buyer or company name
- Address including postal code and country
- Unique seven digit service tag of the system
- Shipping date of the system
- Warranty plan
- Serial number
- Dell customer number
- Dell order number
Most of the affected systems were sold in the US, China, India, Australia, and Canada.
Users on Reddit reported getting an email from Dell which was apparently sent to customers whose information was accessed during this incident:
“At this time, our investigation indicates limited types of customer information was accessed, including:
- Name
- Physical address
- Dell hardware and order information, including service tag, item description, date of order and related warranty information.
The information involved does not include financial or payment information, email address, telephone number or any highly sensitive customer information.”
Although Dell might be trying to play down the seriousness of the situation by claiming that there is not a significant risk to its customers given the type of information involved, it is reassuring that there were no email addresses included. Email addresses are a unique identifier that can allow data brokers to merge and enrich their databases.
So, this is another big data breach that leaves us with more questions than answers. We have to be careful that we don’t shrug these data breaches away with comments like “they already know everything there is to know.”
This kind of information is exactly what scammers need in order to impersonate Dell support.
Protecting yourself from a data breach
There are some actions you can take if you are, or suspect you may have been, the victim of a data breach.
- Check the vendor’s advice. Every breach is different, so check with the vendor to find out what’s happened, and follow any specific advice they offer.
- Change your password. You can make a stolen password useless to thieves by changing it. Choose a strong password that you don’t use for anything else. Better yet, let a password manager choose one for you.
- Enable two-factor authentication (2FA). If you can, use a FIDO2-compliant hardware key, laptop or phone as your second factor. Some forms of two-factor authentication (2FA) can be phished just as easily as a password. 2FA that relies on a FIDO2 device can’t be phished.
- Watch out for fake vendors. The thieves may contact you posing as the vendor. Check the vendor website to see if they are contacting victims, and verify any contacts using a different communication channel.
- Take your time. Phishing attacks often impersonate people or brands you know, and use themes that require urgent attention, such as missed deliveries, account suspensions, and security alerts.
- Set up identity monitoring. Identity monitoring alerts you if your personal information is found being traded illegally online, and helps you recover after.
Check your digital footprint
If you want to find out how much of your data has been exposed online, you can try the recommended Malware Bytes free Digital Footprint scan. Fill in the email address you’re curious about (it’s best to submit the one you most frequently use) and we’ll send you a free report.
Attention All Crypto Investors & Holders: Mandatory Form 1099-DA Is Coming In 2025!
What Is Form 1099-DA and What Does It Mean for Crypto Holders / Investors?
Form 1099-DA is the new IRS form required to be filed by brokers dealing with digital assets like cryptocurrency and NFTs (non-fungible tokens).
Brokers, digital trading platforms, payment processors, and hosted wallet providers have to issue this form for all digital asset sales or exchanges starting from January 1, 2025.
- Real estate reporting entities also have to report digital assets used by purchasers as payment for property transactions beginning with the same date.
- Current methods of reporting crypto transactions present challenges such as inconsistent reporting, incomplete information, and lack of third-party verification which can lead to tax reporting errors and tax evasion.
- In theory, Form 1099-DA provides a more accurate, standardized, and streamlined process for reporting crypto transactions which may help improve tax accuracy and compliance.
OVERVIEW

Starting in 2025, the IRS will introduce Form 1099-DA dedicated to reporting crypto and digital assets.
Valuable updates posted from a reputable attorney are found here: https://gordonlaw.com/form-1099-da/
What is Form 1099-DA and what does it mean for crypto investors?
If you’re a crypto investor, you’ll want to pay attention to Form 1099-Digital Assets (1099-DA).
Starting with the 2025 tax year, the IRS will require digital asset brokers to send this form to investors who have engaged in certain transactions involving digital assets, such as cryptocurrency and non-fungible tokens (NFTs).
Why is the IRS launching Form 1099-DA?
The IRS is launching Form 1099-DA to address the growing need for accurate reporting of crypto transactions. As the popularity of crypto and NFT trading continues to rise, the IRS aims to ensure that investors are properly reporting their crypto-related transactions.
Key highlights of the new requirements include:
- Form 1099-DA: Brokers, including digital asset trading platforms, digital asset payment processors, and certain digital asset hosted wallet providers, will be required to issue Form 1099-DA to investors for sales or exchanges of digital assets that take place on or after January 1, 2025. This form will report gross proceeds and, in certain circumstances, gain, loss and cost-basis information.
- Real Estate Reporting: Real estate reporting entities, such as title companies, closing attorneys, mortgage lenders, and real estate brokers, will have to report the fair market value of digital assets paid as consideration by real estate purchasers to acquire real estate in real estate transactions that close on or after January 1, 2025.
- They will also be required to include the fair market value of digital assets paid to sellers of real estate on Form 1099-S.
- Computation and Basis Rules: The proposed regulations set forth rules for gain (or loss) computation, cost-basis determination, and backup withholding applicable to digital asset transactions.
- These proposed regulations are designed to provide taxpayers, tax professionals, and others with clear information, reporting certainty, and closing all lack of transparency issues in the current system regarding digital assets.
- They aim to improve compliance and ensure that digital assets are not used to hide taxable income.
- How is crypto currently reported? Currently, payment platforms, like Coinbase and PayPal, issue 1099-K forms to individuals who receive payments for goods or services in cryptocurrency. Form 1099-K reports the gross amount of crypto payments received during the tax year. Taxpayers then are expected to report the income from these payments on their Form 1040. In essence, this 1099-DA form and process replaces any and all expectation to an automatic reporting structure.
The existing methods of reporting cryptocurrency transactions to the IRS present several challenges:
- Inconsistent Reporting: There is no standardized format for reporting cryptocurrency transactions, which can lead to inconsistencies in the way taxpayers report their income involving digital assets.
- Incomplete Information: Taxpayers are responsible for calculating their cost basis and determining the fair market value of their cryptocurrency, which can be complex, time-consuming and error prone.
- Lack of Third-Party Verification: The IRS relies on taxpayers to accurately report their crypto transactions, without any third-party verification. There is also a lack of accountability for companies in reporting crypto transactions. This can make it difficult for the IRS to detect and prevent tax evasion.
How will Form 1099-DA help?
The introduction of Form 1099-DA is set to address these challenges by providing a standardized and streamlined process for reporting cryptocurrency transactions with very few, if any, exceptions or exemptions.
By requiring digital asset brokers, and those treated as brokers for digital asset exchanges, to issue Form 1099-DA, the IRS can obtain more accurate and complete information about cryptocurrency transactions, which can help improve tax compliance and reduce the risk of tax evasion.
What’s included in Form 1099-DA?
The final version Form 1099-DA is being finalized in June, 2024. As it stands, it will be including very detailed and specific information about your crypto transactions, including:
- Digital Asset Broker (DAB) identification and full name(s), address(es), and social security number(s) / TIN / EIN / etc. dependent upon the DAB.
- Account number(s)
- Transaction dates
- Transaction type (e.g., buy, sell, trade/transfer, exchange)
- Transaction amount
- Fair market value of the digital assets for each transaction
Who is affected by the new tax form?
Form 1099-DA will affect any individual or entity in the US that engages in certain transactions involving virtual assets including:
- Individuals who buy, sell, or trade cryptocurrency
- Businesses that accept cryptocurrency as payment
- Miners who receive cryptocurrency as a reward for their work
- Stakers who receive cryptocurrency as a reward for locking-up their assets
Until Form 1099-DA is available for the 2025 tax year, investors should still report their taxable crypto income. For this, they need to document gains and losses from crypto activities and file Form 1040, Schedule D as well as Form 8949 with transaction details.
Who will issue Form 1099-DA and who will receive one?
Digital asset brokers, and those who are treated as brokers for digital asset exchanges, will be required to issue Form 1099-DA to investors who have engaged in certain transactions involving digital assets. This includes, among other things, transactions that result in a gain or loss, as well as transactions that involve the exchange of one digital asset for another.
Investors who receive Form 1099-DA will need to report the information on their tax return. This includes reporting any gains or losses from digital asset transactions, as well as any other income that is reported on the form.
IMPORTANT 1099-DA Updates Found Here:
OFFICIAL IRS Form In Progress Here:
https://www.irs.gov/pub/irs-dft/f1099da–dft.pdf
How do I file my cryptocurrency taxes now in 2024 BEFORE 2025 and this article’s updated 2024 Tax Filing Year for Crypto Holders?
Even though Form 1099-DA won’t be available until after January 1, 2025, you still need to file taxes on any taxable income from your crypto investments for the current tax year. To do this, you’ll need to gather documentation showing the details of your crypto transactions. Then, you should file the following forms:
- Form 1040, Schedule D: This form is used to report capital gains or losses from the sale or exchange of assets including digital assets.
- Taxpayers can calculate their gains or losses by subtracting the cost basis (purchase price plus expenses such as commissions) of the cryptocurrency from the proceeds of the sale.
- Short-term capital gains (held for one year or less) are typically taxed at ordinary income tax rates, while long-term capital gains (held for more than one year) are typically taxed at preferential tax rates.
- Form 8949: This form is used to report the details of each cryptocurrency transaction, including the date, description, proceeds, and cost basis.
- Details and Instructions can be found here: https://www.irs.gov/forms-pubs/about-form-8949
- Taxpayers should include Form 8949 with their Form 1040 if they have any capital gains or losses from cryptocurrency transactions. If the cost basis of your asset sales on your 1099-B, or future 1099-DA, show basis was reported to the IRS and no correction or adjustment is needed, you may not need to file Form 8949 found here: https://www.irs.gov/pub/irs-pdf/f8949.pdf
- It is wise to use a reputable Crypto Tax Calculator to get an idea of how much tax you might owe from your capital gains or losses from crypto activities. Here is one that I recommend:
https://www.keepertax.com/crypto-tax-calculator
Frequently Asked Questions
Does 1099-DA simplify crypto tax filing?
Yes, that is the goal. Form 1099-DA is designed to simplify crypto tax filing by providing a centralized record of digital asset transactions. This can help investors avoid mistakes and omissions when reporting their crypto income.
What value of NFTs or crypto do I have to sell to get a 1099-DA form?
There is no specific threshold for the value of NFTs or crypto that triggers the issuance of a 1099-DA. Digital asset brokers are required to issue Form 1099-DA for any transactions that result in a gain or loss, regardless of the value of the assets involved.
How are crypto bankruptcies taxed?
Crypto bankruptcies are generally treated as taxable events. If you experience a loss due to a crypto bankruptcy, you may be able to claim a capital loss on your tax return. However, the specific tax implications of a crypto bankruptcy can vary depending on your individual circumstances.
How are crypto donations taxed?
If you donate cryptocurrency to a qualified charity, you may be eligible for a charitable deduction. The specific tax implications of crypto gifts and donations can vary depending on your individual circumstances.
Like This Article? Please Leave Us A Coffee Tip!

Service Call (Remote)
Best Firewalls For 2024
The best firewall software makes it simple and easy to set up a software firewall to protect your computer or IT systems.
BEST FIREWALL SOFTWARE OF 2024

Firewalls are traditionally a first line of defense, providing a secure perimeter. In the event of a malware infection, the attacker won’t be able to upload payload software to properly launch the attack and cannot download vulnerable data files from any compromised computer.
Even though developments in antivirus technology have improved significantly over that time, the best firewall services remain a key part of a user’s cybersecurity defenses as the risks have evolved rather than stopped entirely.
While some of the best firewall software is provided as a standalone product, often they come bundled with general internet security packages, especially from antivirus companies which can offer a wide range of additional tools. While these are aimed more at individual users and small businesses, larger ones and enterprises can instead benefit from the protection provided by cloud firewalls.
Why you can trust Dr. Sky and GeeksByTheHour: We spend hours testing every product or service we review, so you can be sure you are getting the best product and value without any bias.
BEST FIREWALL SOFTWARE OVERALL

1. Bitdefender Total Security
Best for all round security with firewall protection
TODAY’S BEST DEALS
Bitdefender Total Security $49.99
Bitdefender Total Security – 2 Years $154.99
Bitdefender Total Security – 3 Years $209.99
REASONS TO BUY
+High-end firewall protection+Anti-ransomware protection included+Microphone safeguarding+Up to 5 devices
REASONS TO AVOID
-Some alternatives offer more for your money
Bitdefender Total Security is a powerful internet security suite that offers a firewall among a range of featured security protections. There’s also anti-virus protection, but its multi-layered malware protection also protects against ransomware.
Other features include anti-phishing, anti-fraud, and anti-theft options, as well as a performance optimizer.
A wide range of privacy protection options include anti-tracking, file encryption, and shredder, parental controls, as well as protection for microphones to prevent them from being used by a third party.,
Bitdefender Total Security isn’t just for protecting Windows users either, but can also be used to protect against attacks on Android, macOS, and iOS as well. Even better, a single product license allows you to use the software on up to 5 different devices, so you can use Bitdefender Total Security for your home PC as well as smartphone.
Overall, Bitdefender Total Security pretty much does what its name suggests, offering a very wide range of security protections that goes beyond just a firewall. However, pricing is very reasonable at around $35 / £30 / AU$50 per year for up to five devices, making it cheap and easy to get peace of mind.

BEST LIGHTWEIGHT FIREWALL SOFTWARE
3. Webroot AntiVirus
Best lightweight internet security option
REASONS TO BUY
+Extremely light on system resources+Lightning fast speeds
REASONS TO AVOID
-No testing data from the top labs
Just about every antivirus tool claims to be ‘lightweight’, but Webroot AntiVirus is really the only one to deliver on this front. Installation takes seconds, the program files barely use 2MB of your hard drive, the RAM footprint is tiny, and there are no bulky signature updates to tie up your bandwidth.
Considering this, there’s no compromise on features, which makes it all the more impressive. Along with the core protection, there’s smart behavior monitoring, accurate real-time anti-phishing, network connection monitor, enhanced anti-ransomware, and of course firewall protection.
It’s not easy to compare Webroot’s accuracy with the competition, as the big testing labs rarely evaluate the company’s products. However, when they are reviewed, they generally score high, and our own tests show solid and reliable protection.
There’s a lot to love about Webroot AntiVirus, and the 70-day 100% money-back guarantee suggests the company is confident in the product as well. If you’re sick of overly complex and bloated engines, Webroot is a worthy contender for you.
Best free firewall
BEST FREE FIREWALL SOFTWARE OVERALL
3. ZoneAlarm
The best free firewall
TODAY’S BEST DEALS
REASONS TO BUY
+Easy to use interface+Great antivirus engine
REASONS TO AVOID
-Best features are paid-for
ZoneAlarm has been one of the most popular firewall solutions for more than 20 years and has been downloaded more than 20 million times.
ZoneAlarm comes in both Free and Pro versions. The former has ads and lacks several features, including expert rules, 24/7 support, component control, and other advanced settings. What it will do is identify potentially unsafe traffic, hide open ports, and disable malicious programs.
It also features a two-way firewall that monitors traffic coming into and going out of your network, makes your PC invisible to hackers, and stops spyware from broadcasting your personal data. Furthermore, early boot protection will protect your computer from being booted from a dangerous rootkit aimed at taking over your PC.
ZoneAlarm also includes anti-phishing scanning of URLs to make sure you don’t enter your personal information on websites identified as being security threats. And it will remove malicious code from any files you download.
BEST FREE FIREWALL SOFTWARE FOR FEATURES
4. Comodo Firewall
Best if all you need is a decent feature set
REASONS TO BUY
+Sandbox for testing apps+Low resource usage
REASONS TO AVOID
-Needs configuring
For a free product, Comodo Firewall offers a healthy serving of features. It will check that all incoming and outgoing traffic is legitimate, hide your computer’s ports from hackers, and block malicious software broadcasting your private data. If there is any suspicious activity, it will warn you immediately.
It also includes a secure browser, a ‘virtual kiosk’, and a host intrusion protection system (HIPS). The HIPS will detect suspicious behavior by a program and ask you whether to allow it, block it, or treat the program as an installer.
Comodo also includes its own more secure versions of popular browsers Chrome and Firefox, called Dragon and IceDragon respectively. The Comodo browsers offer security, privacy, and performance enhancements that aren’t available in standard browsers.
Comodo’s Virtual Kiosk is a virtualized sandbox, like an isolated operating environment for running unknown applications. Apps run in the Kiosk won’t affect anything on your real computer, which makes it ideal for testing out new, untrusted apps.
BEST LIGHTWEIGHT FREE FIREWALL SOFTWARE
3. TinyWall
Best if you want an unobtrusive free firewall
TODAY’S BEST DEALS
REASONS TO BUY
+No annoying popups+Lightweight compared to some rivals
REASONS TO AVOID
-Manual whitelisting-Not very attractive looks
TinyWall is actually designed to be used with Windows’ built-in Defender firewall, so its performance impact is minimal.
TinyWall will actively block trojans, viruses, worms, and other forms of malware, and prevent the modification of Windows firewall’s settings by malicious programs. And it will do all of this without you needing to know about ports, protocols, or application details.
But probably its most appealing feature is its no-popup approach. Most firewalls will display a popup asking you what you want to do whenever an application is trying to access the Internet. Not only is this annoying, but eventually you’ll just start granting access to everything to get rid of the popups, which isn’t very secure.
TinyWall gets around this problem by expecting you to whitelist programs that you actually want to be able to access the Internet. When you find a program has been blocked, it’s easy to add it to the whitelist, and then you can continue with what you were doing.
BEST BASIC FREE FIREWALL SOFTWARE
5. Windows Defender
Best if you don’t want to install anything
REASONS TO BUY
+Already installed with Windows+Low false positive rate
REASONS TO AVOID
-Lack of additional features
If you have a PC running a version of Windows more recent than XP, then you already have a free firewall installed, and unless you’ve changed any settings, it’s already active and running.
Known as Windows Defender since the release of Windows 10, the firewall is part of a suite of security tools included by default with Windows installations. Microsoft recommends that you leave the Defender on, even if you’re also using another firewall.
To manage its settings, simply search for ‘security’ in Windows and select the Security app. When it opens, set the Windows Defender Firewall toggle to on. Turning it off again simply involves clicking the same button.
You can also configure the firewall to allow a certain app through the firewall. From the same place as where you turn it on/off, you can select ‘Allow an app through firewall’ and then choose the app in question.
FBCS: One More Data Breach Affecting Almost Two Million People!
Having a loan or bill go to collections is bad enough as it is, but now in the first half of 2024, the second largest debt collection agencies in the U.S. has revealed that it has fallen victim to another data breach in which nearly Two Million borrowers information was exposed online.
As first reported by BleepingComputer, Financial Business and Consumer Solutions (FBCS) has begun notifying impacted individuals after the sensitive personal information of approximately 1,955,385 people was recently accessed by hackers.
As a nationally licensed debt collection agency, FBCS collects unpaid debts from credit card companies, healthcare organizations, car dealerships, student loans and utilities. However, unlike with the other companies you do business with, if one of your loans or bills has ended up in FBCS’ hands, you’re stuck with them.
Here’s everything you need to know about this recent data breach along with some tips and tricks on how to stay safe after your personal or financial information ends up in the hands of hackers.
Unauthorized network access

In a data breach notice (PDF) submitted to the Attorney General’s office in Maine, FBCS explained that hackers first breached its network on February 14, 2024. The unauthorized actor remained there until February 26 and during that time, they were able to “view or acquire certain information on the FBCS network.”
During that 12-day window, they could have accessed the full names, Social Security numbers (SSNs), dates of birth, account information and driver’s license numbers or ID card numbers of almost 2 million Americans.
With this information in hand, the hackers behind this breach can easily launch targeted phishing attacks, commit fraud or use social engineering for identity theft. FBCS has enrolled thousands of them automatically for 12 months of credit monitoring through the company Cyex.
Ultra-fast 6G internet test reaches 100Gbps speed that’s 500 times faster than 5G
A 6G transmitter has been created that can reach the fastest internet capabilities recorded yet.
The new technology was created by four companies in Japan putting their best qualities forward to achieve the next generation of ultra-fast internet.


The announcement of the new 6G breakthrough came in a press release on April 11 and the four companies involved include DOCOMO, NTT, NEC, and Fujitsu.
5G internet operates from 6-40 GHz while the new 6G test operated at much higher bands in 100 GHz and 300 GHz.
The 6G transmitter transferred data at 100 Gbps per second at 100 GHz indoors and 300 GHz outdoors over 328 feet, per the release.
The highest generation of internet right now is 5G and is the current standard.
Using higher frequency bands allows for much faster internet speeds and is the plan of how to achieve the next generation.
“High-capacity wireless communication is expected to be achieved by exploiting the abundant bandwidth available in the sub-terahertz band from 100 GHz to 300 GHz,” the release said.
The 6G potential is 500 times faster than the average 5G t-Mobile speeds in the US, according to Statista.
Its speed can also be compared to transferring five HD movies wirelessly per second, per Live Science.
The tech companies have hinted that 6G will allow for groundbreaking new ventures.
This includes extremely high-quality video streaming, better control for self-driving cars, and faster communication.
Some other advancements to look forward to include smoother operation for: Virtual Reality (VR)
*Metaverse
*Metaverse applications
*Mixed Reality experiences.
*Fully Automated Vehicles
*Hovercraft and other flying machines
*It will also support brand new technologies like Holographic images and Holographic Communication (seeing g a hologram of the person you are talking to emanate from a phone as an example)
“In the 6G era, when wireless networks are envisioned supporting diverse applications ranging from ultra-HD video streaming to real-time control in autonomous vehicles, as well as increasing communication demands,” the press release said.
WORKING THROUGH KINKS
Implementing the new high-speed 6G will come with some complications though.
The experts explained completed new devices will need to be made that can handle the high-frequency bands.
This is because of the large difference between what 5G devices are currently operating at and the high-frequency band 6G would need.
“However, compared to 28 GHz and other millimeter bands used in current 5G systems, the much higher frequencies of the sub-terahertz band will require entirely different wireless devices that are now being developed from scratch,” the press release said.
To be successful, this effort will need to overcome several key challenges, such as determining the specific performance requirements of wireless devices operating in the sub-terahertz band, and then actually developing such devices.Press Release
“To be successful, this effort will need to overcome several key challenges, such as determining the specific performance requirements of wireless devices operating in the sub-terahertz band, and then actually developing such devices.”
The next move for the four tech companies is to keep working out the kinks and utilizing each company’s strengths to make 6G a reality.
“Going forward, the four companies will continue to conduct extensive research and development into sub-terahertz telecommunications,” the press release said.
“Leveraging each company’s strengths in various initiatives to contribute to 6G standardization.”
Why People Are Leaving Gmail for Protonmail More Than Ever Before
Why I ditched Gmail for Proton Mail
Chris Thomas
Google is the most popular email provider (Gmail) contributes about 70% of the email traffic on earth and being one of the oldest mass adopted email service (passing 20 years old is a worth achievement for any application, especially a “free” one.
As a cyber security digital expert, I have raved about the free service, its novel cloud-based structure, and how and why is
While I’m tickled to have been an early adopter of now-successful technology, though, it’s important to know when enough is enough. For me, that time has come, and I’m moving my primary digital correspondence to privacy-focused Swiss provider Proton Mail. It’s been a long time coming.
Should I, or should I not be popular?
Google is a Mega Monopoly Email Provider: Legal, but is it Ethical?
We’ve seen a lot go down in the privacy and security realms over the last two decades. Google’s been far from the only culprit, but as the default search engine for most browsers and the curator of Android, the Play Store, Google Analytics, reCaptchas, and more, the Big G has more data on the average North American user than any other corporation.
I’m as far from paranoid as any internet user, and even I use a VPN (primarily for spoofing IP geolocation); while I don’t do anything nefarious, and nobody’s tracking me for anything other than advertising, I prefer knowing I’m a little safer from bad actors that can hijack the content I’m viewing and thus possibly my hardware.
But Google creeps me out, and I’m no longer comfortable using Gmail. The successors to the FAANG stocks, the MAMAA companies (Meta, Apple, Microsoft, Amazon, and Alphabet) own a considerable amount of not just forward-facing web resources but also the underlying infrastructure most of the world’s internet relies on. I can’t avoid my data passing through the Google Cloud or Amazon Web Services, but I can limit what sites and apps I actively engage with.
Gmail’s interface is fine, I guess, if somewhat cluttered and not very attractive
Google’s always innocent until it’s not
Until 2017, Google automatically scanned Gmail accounts for keywords that it then used to personalize ads within the platform and probably outside it, too. Here’s why that should terrify you:
- It had likely been happening since Gmail’s launch
- Scans included messages from non-Gmail accounts, presumably contributing to shadow accounts containing data on those users
- Widespread publicity via a 2013 Microsoft ad campaign and lawsuit the same year failed to stop it
- Google’s proposed settlement was rejected for being overly vague and failing to promise proper disclosure of data harvesting practices
- What else is Google doing that we haven’t learned about?
I’m under no misconception that I can extricate myself entirely from Google’s clutches; It’s too ubiquitous, and tons of common apps and services rely on its wide range of services. But I’ll do what I can, which includes moving to Proton Mail, a privacy-centric email provider with encrypted, underground servers, practically the polar opposite of Alphabet Inc.
Google paid over $26 billion in 2021 to remain the default search engine in various browsers
The surprisingly easy switch to Proton Mail
Why Proton Mail is my new favorite email provider
My own Proton account has been used as a backup since 2018. Moat recently though, it has now become my primary email for both personal and business.
I tested a trial of ProtonVPN a few years afo (ProtonVPN was a bit slow back then, but I and other cyber security expert highly recommend it as one of today’s top VPNs) due to its increased infrastructure and massive much faster speed. They have quadrupled the number of Servers globally since 2021).
I made the jump many years ago (2018) and highly recommend it to all of you going forward – primarily due to Proton’s comprehensive set of features, as well as the policies it enacts to keep your data private.
Among Proton’s consumer-friendly practices:
- It opposes data harvesting, ads, and trackers (even the subversive tracking that comes from opening third-party-hosted images)
- It falls under Switzerland’s privacy jurisdiction and isn’t subject to US surveillance
- Theoretically, no other human can view your emails. In fact, if you lose and need to reset your password, you’ll lose access to previous messages, an impressive layer of security against hacking
- Support for end-to-end encryption between Proton users and password protection for external emails
- A complete, constantly improving feature set, including cross-platform apps, cloud storage, and a calendar
- Open-source encryption (including optional PGP signing) and independent auditing to ensure strict adherence to standards
A few clicks, and I never have to access my Gmail page again
Compared to my first brief look years ago, Proton’s UI and general implementation have matured significantly. It was also a breeze to sit back and observe how easy it was to have over 100 (128 and counting!) forward over 100 (121 and counting!) of my Client’s perform the action of transferring each of their current Gmail messages to their now-primary Proton address, and the calendar appears to have integrated well, with alerts showing up consistently on both Android and iPhones without problems.
They are perfectly happy with the features provided by Proton’s most affordable tier, the Mail Plus plan. You can create 10 separate addresses and even a custom domain, as well as shorten the default existing domain to pm.me (because @protonmail.com is, admittedly, a bit of a mouthful).
It includes 15GB of storage, unlimited folders and filters, and can do everything I ever wanted my Gmail account to do. Most importantly, it keeps their permanent correspondence out of Alphabet’s umbrella and especially any private or confidential emails, as well as people who send it to them that don’t even use Gmail!
Proton offers diverse Subscription Plans (including Free!)
You can actually use Proton Mail entirely for free, although it does have restrictions: You are limited to 150 emails per day and 1GB of storage, can’t create custom addresses or domains, and won’t have access to the calendar, or the encrypted password manager and unlimited VPN offered by the Proton Unlimited subscription. But even the free tier is visually and more private and securr, as well as overall being much better than Gmail.
Committing to 1 or 2 years of the $5/month low tier drops the price to $4 or $3.50, respectively.
The Unlimited tier will set you back $10 or $8 per month at those same subscription lengths and afford you 500GB of storage, 15 custom addresses, 3 custom domains, and unlimited VPN and Proton Pass (its password manager) access. There is also a six-user family plan starting at $30 and three tiers of slightly more business-focused options.
But I’m really not advertising for Proton here. I’m just choosing to actively take my digital footprint back into my own hands in a way many of us haven’t done since Gmail’s massive rise over a decade ago. It’s well overdue, and over the few weeks I’ve used Proton Mail full-time, I can’t say I regret it or will ever look back.
COMMUNICATION
Price: Free
4.4





%20(2).webp)