How to Track Anyone’s IP using Images? — Email, QR Code, PDF, EXE, MS Word, MS Excel, & any file can be a “digital mouse trap”..
Supported Tokens: HTTP, DNS, Web Image, Cloned Website, Adobe PDF, MS Word, MS Excel, MySQL Dump, Windows Directory, Custom EXE, QR Code, Sensitive Command, SVN, AWS API Keys, Fast Redirect, Slow Redirect, SQL Server, and many more…
Follow DigitalFoundation on Telegram for more..
Greetings, World!
Today I’ll teach you how to track anyone’s IP using Transparent Images! Yeah..
We will first understand the whole concept then redirect towards the step by step usage guide. You can even do this manually using custom developed payloads but it’s a more better way to do this easily. I’ll help you with that today, by providing easy steps you can follow. Let’s start learning..
Understanding Canarytokens
Canarytokens are like digital traps for your computer systems. They work by watching for certain actions, such as someone reading a file, making a database query, running a process, or spotting specific patterns in log files. It’s similar to those tracking images in emails, but instead of tracking opens, it tracks actions on your system.
The cool thing is, we can use Canarytokens to set up these traps in our regular computer systems, kind of like putting alarms in different parts of your house where anything someone does can set off an “alarm” – or at least a notification.
Now, why should you bother with these Canarytokens? Well, sometimes hackers get into computer networks, and it happens to big companies, governments, regular people — basically, everyone. That part is understandable. But what’s not okay is only finding out about it way later, like months or even years down the line which seems disappointing!!
Canarytokens are a free, easy, and fast way to help you know right away if someone is messing around in your systems. It’s like the hackers accidentally letting you know they’re there.
- Web bug / URL token — Alert when a URL is visited
- DNS token — Alert when a hostname is requested
- AWS keys — Alert when AWS key is used
- Azure Login Certificate — Azure Service Principal certificate that alerts when used to login with.
- Sensitive command token — Alert when a suspicious Windows command is run
- Microsoft Word document — Get alerted when a document is opened in Microsoft Word
- Microsoft Excel document — Get alerted when a document is opened in Microsoft Excel
- Kubeconfig token — Alert when a Kubeconfig is used
- WireGuard VPN — Alert when a WireGuard VPN client config is used
- Cloned website — Trigger an alert when your website is cloned
- QR code — Generate a QR code for physical tokens
- MySQL dump — Get alerted when a MySQL dump is loaded
- Windows folder — Be notified when a Windows Folder is browsed in Windows Explorer
- Log4Shell — Alert when a log4j log line is vulnerable to CVE-2021–44228
- Fast redirect — Alert when a URL is visited, User is redirected
- Slow redirect — Alert when a URL is visited, User is redirected (More info is grabbed!)
- Custom image web bug — Alert when an image you uploaded is viewed
- Acrobat Reader PDF document — Get alerted when a PDF document is opened in Acrobat Reader
- Custom exe / binary — Fire an alert when an EXE or DLL is executed
- Microsoft SQL Server — Get alerted when MS SQL Server databases are accessed
- SVN — Alert when someone checks out an SVN repository
- Unique email address — Alert when an email is sent to a unique address
Step-by-Step Usage
Go to canarytokens.org & choose your Canarytoken. This is like setting up a digital trap. Provide an email where you want to be notified and a note to remind yourself where you placed it.
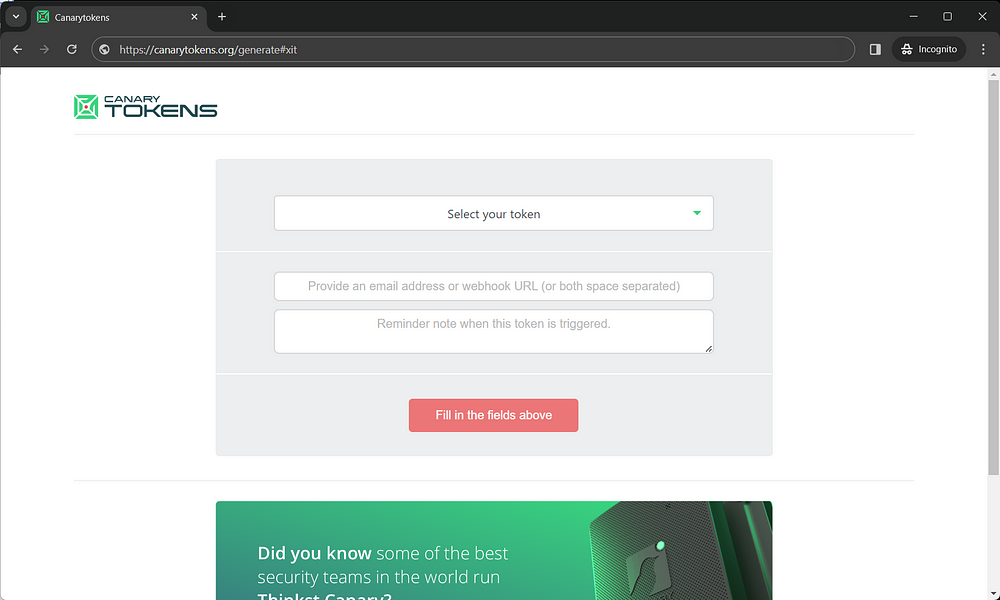
Generate a Canarytoken, which is a unique URL or Fast redirect or anything else – it is all your choice. It’s like creating a secret link that will trigger an alert if someone interacts with it. In this blog I’ll be using Fast redirect as an example.
 EXAMPLE
EXAMPLE
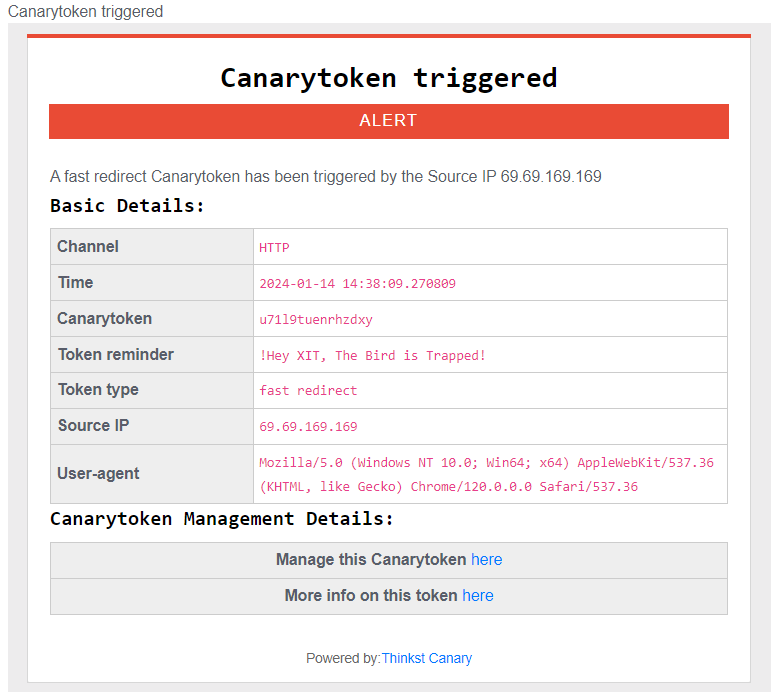
Put the generated Canarytoken in a special location & send it to the target. It could be in an email, a document, or even as an embedded image. If a target arrives upon it, you’ll receive an email notification, alerting you that something is off – just like a mouse activating a mouse trap :–)

Clicked..Your Digital Mouse Trap Is Set!

If your target hits the URL/File, like shown in the example above, your token gets activated & alerted to email or webhook as below:
You can also rename the generated PDF/Excel/Word document without affecting its operation!